The gang at Participatory Culture have just released Democracy Internet TV -- digital "television" as it should be, where we're both viewers and broadcasters. "Democracy" is a multi-platform combination RSS-reader/video player that helps you get the video you want, when and where you want it.
The Democracy internet TV platform is a free and open way to watch, share, and broadcast video on the internet. You can read about it below or get right to it: Get Democracy.
Note to self (and Google, which didn't have any answers on the subject when I looked): To send mail through the Speakeasy mailserver from the Treo, configure Versamail to use port 587, along with ESMTP authentication (in the "Advanced" options).
I had to reconfigure after Versamail munched my old settings.
Student Senate, this time. Gavin Baker, of Florida's Free Culture movement is running for Student Senate. I met Gavin at the recent Data Devolution conference. His platform, including open access publishing and a healthy debate about peer-to-peer technology on campus sounds good for Florida (home of the infamous ICARUS), and for a broader audience.
A world-class university deserves world-class technology. Technology affects virtually every aspect of students' lives, but all too often, student needs are overlooked. As a senator, I will work to represent the concerns of all students.
If you're at the University of Florida, consider voting for Gavin. If you're a student elsewhere, consider running as or supporting your own Free Culture candidates. If you're of national voting age, try to get state and national representatives thinking about technology issues too.
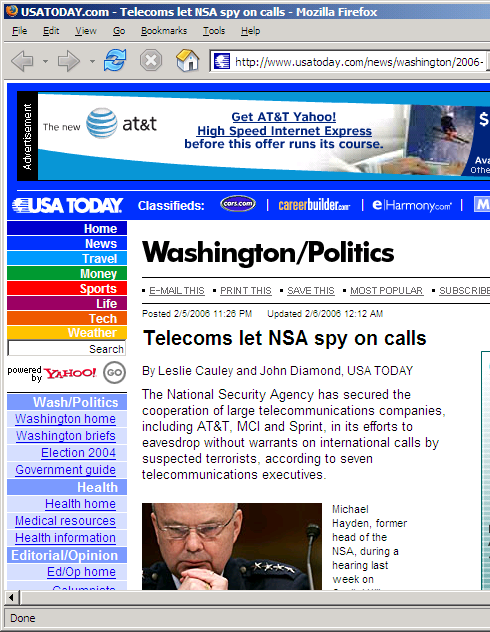
Unfortunately, I don't have confidence that the filtering techniques being used on warrantless interceptions and datamined communications will be any more accurate than the algorithm that placed this AT&T ad above a story on "Telecoms let NSA spy on calls." The story does feature AT&T prominently, just not in a way that has me rushing to buy service from them...
Back in November 2004, Perfect 10 lobbed a complaint at Google, asserting that the search engine should be liable for indexing infringing images that others had posted. Yesterday, the California Central District issued an order (local copy) that's a mixed bag, but gets a lot right in its description of how copyright works on the web.
The court grants in part and denies in part Perfect 10's motion: it finds Google's inclusion of thumbnails of P10 images infringes, but the inclusion of links to infringing sites or the inline framing of infringing sites do not. First the good: The court holds that linking to infringing sites does not subject Google to liability, even if Google makes money from some of those sites via AdSense. Users visiting infringing sites via Google are not direct infringers, the court says.
It also holds that showing third-party pages inline, as Google image search does via frames when a user clicks a thumbnail, does not count as an infringing "public display" by Google. These results make sense. The infringement, if any, takes place on third-party sites and the search engine should not be held liable for their activities. Most warming to my heart, the court found it entirely unnecessary to reach the question of DMCA safe harbors, for there was no liability against which Google needed harboring.
The court is less solid on its analysis of Google's thumbnailing, there finding that the result should diverge from the factually similar Kelly v. Arriba Soft because Google's AdSense made the search more "commercial" and because P10 had licensed some thumbnails to Fonestarz (after filing suit, natch), to show effect on the market. The court left it to Google and P10 to compromise on an injunctive order. Google plans to appeal.
The NYT updates the story of the "Lazy Sunday" sketch: after finding new life for Saturday Night Live in a mock rap segment that spread "virally" far beyond the television sets, NBC sent out the copyright squads. They sent cease-and-desist letters to hosting sites such as YouTube, whose copy of the video had risen to the top of a Google search.
Julie Summersgill, a spokeswoman for NBC Universal, said the company meant no ill will toward fan sites but wanted to protect its copyrights. "We're taking a long and careful look at how to protect our content," she said.
...
Several online commentators noted that NBC's response to YouTube, while legally justified, may have been short-sighted. The online popularity of "Lazy Sunday" has been credited with reviving interest in "Saturday Night Live" at a time when it is in need of some buzz.
I'm sure NBC lawyers need no reminding that unlike trademarks, copyrights do not need to be policed to retain their validity. Instead, NBC seems to be shutting down its own best advertising.
Apple's DMCA takedowns to web sites discussing the new Intel operating system -- and ways to get it running on non-Mac hardware -- have been in the news lately. Now, Chilling Effects has the notices sent to two of the sites' ISP, and what they don't say is as interesting as what they do. (Notices sent regarding the OSx86 Project and Win2osx.)
Both letters claim that "Apple uses encryption and other technological measures in Mac OS X ver. 10.4.4 to effectively control access to its copyrighted operating system code and to effectively protect its rights as a copyright owner in that code." Apple says hacks to enable OS X to run on non-Apple hardware "are primarily designed and produced for the purpose of circumventing those technological measures," in violation of the anticircumvention provisions of the DMCA.
Apple claims further that the Win2osx site posted pieces of Apple's copyrighted code -- but it does not make the same claim against OSx86. The most it can claim is that the OSx86 site linked to a third-party site (Maxxuss, hosted in Russia, down as of this posting) offering circumvention code and copied code. The ISP gets a notice as host to a linker, at best a tertiary connection to the claimed infringement or circumvention (but one in the United States and easy to find).
The OSx86 Project is back, minus links to the Maxxuss site. But at bottom, was Maxxuss infringing or circumventing? Clearly it was doing something Apple would prefer not be done, offering users a way to unbundle OS X software from Mac hardware. But isn't that the kind of reverse engineering for interoperability that is fair use under copyright law and was supposed to be preserved in the DMCA? Provided users of the Maxxuss patches had validly licensed copies of the OS, their use should be a matter of their own choice and the terms of their OS X licenses, but not a circumvention. Once again, anticircumvention offers a big hammer for those who want to break interoperability.
There's been lots of muddle over the Google book-scanning project, from confusion over what Google's actually doing to misinformation about the law governing it. Google's asking its users to help clear the air, asking for help correcting the half-truths like the old canard that fair use is a set number of words or percentage of the work.
In a message to the "Support Book Discovery" group, Googlers invite searchers to add sources to the debate:
If you want to help set the record straight, consider this your invitation to get involved. Below are links to resources where you can find accurate information about Google Book Search, copyright and fair use. If you see a misleading article or blog post, we encourage you to write a letter to the editor, post a comment or blog about the facts.
Hmm, I wonder if there's a search engine that offers pointers to reference books that might help in the quest...
One of the bright spots in debate around the adminstration's warrantless NSA suvreillance is a reminder that privacy and the rule of law are bipartisan issues. Republican Arlen Specter has been asking tough questions of Attorney General Gonzales at Judiciary Committee hearings, joined by senators on both sides of the aisle. Last night on The NewsHour, Republican Lindsey Graham expressed his constitutional concerns in the strongest terms:
SEN. LINDSEY GRAHAM: All I can tell you is that the ultimate damage that I want to avoid is a constitutional damage in terms of checks and balances. I want to fight this enemy. I want to make sure our president and our military surveils the enemy. I want to know if American citizens are collaborating with the enemy. We can do that. We must do that.
But the biggest thing that can happen, to me, as a nation is that in the process of fighting the enemy, we give up the processes that makes us free.
We must not fight for freedom abroad by suppressing it at home.
The Washington Post runs a good piece on the NSA wiretaps: Surveillance Net Yields Few Suspects, reporting that most of the wiretaps have led to dead ends -- and that many innocents are being tapped in the process. Although we still have few details of what the surveillance is, the Post discusses some of the datamining technology that sources suggest may be in use.
Jeff Jonas, now chief scientist at IBM Entity Analytics, invented a data-mining technology used widely in the private sector and by the government. He sympathizes, he said, with an analyst facing an unknown threat who gathers enormous volumes of data "and says, 'There must be a secret in there.' "
But pattern matching, he argued, will not find it. Techniques that "look at people's behavior to predict terrorist intent," he said, "are so far from reaching the level of accuracy that's necessary that I see them as nothing but civil liberty infringement engines."
 Martin Varsavsky has just blogged about FON's partnership with Google , Skype, Sequoia Capital, and Index Ventures
as investors. FON is a startup, of which I'm on the board of advisors, that aims to put wireless internet everywhere by linking sharing and commercial installations. This investment will help get FON off to a strong start.
Martin Varsavsky has just blogged about FON's partnership with Google , Skype, Sequoia Capital, and Index Ventures
as investors. FON is a startup, of which I'm on the board of advisors, that aims to put wireless internet everywhere by linking sharing and commercial installations. This investment will help get FON off to a strong start.
As Martin says,
[The investment gives FON] a strategic boost that should help us make this great idea into a great platform for everyone who wants a faster, cheaper and more secure wireless Internet. We'll invest this money in R&D so we can make it quicker and easier to become a FONERO and so that we can expand the number of things you can do with your FON service. Our goal, after all, isn't just to share bandwidth. It's to use the power of people to people networks to create a global wireless network.
I'm somewhat of a techie -- I built my own MythTV instead of buying a TiVo, I run the server this blog sits on (in my living room), and had my wifi shared already, on its own IP apart from my internal network (I'm pleased that my ISP, Speakeasy, [updated:] welcomes FON use). So what's new about FON? FON aims to make it easy for non-techies to join the wifi-sharing community too -- with FON-ready routers for sale and user-friendly installers coming soon, with security taken into account -- and by doing that, it gives all of us more places to connect. You can join as a "Linus," sharing wifi from your broadband connection and getting it free elsewhere on the network; as a "Bill," sharing wifi and getting paid for it (but paying if you want to use others' hotspots); or as an "Alien," paying a reasonable subscription fee to roam on the FON network.
FON is in beta right now -- or, to use a football analogy on this Super Bowl Sunday, we've scored the first touchdown but it's still early in the first quarter, and we've got a good playbook going forward. Techies can get the software up and running, but only as Linuses, so far; non-techies might want to buy a router or wait for the next revision. The Alien and Bill rollouts will come later, as the infrastructure is built out further. If we can get 3,000 Foneros in 3 months of alpha-stage, who knows how many might join the game as we move forward!
Most of us would be put off if a court issued a press release cheering the number of prisoners its judges had put behind bars or the number of tenants it had helped landlords to evict. That seems antithetical to the neutral adjudication of disputes, and ethical rules regularly decry such "appearance of bias." Yet WIPO seems to think it perfectly natural to crow about its arbitrators' favoritism for complainants against "cybersquatters" in UDRP proceedings. It issued a release that reads like a solicitation for trademark claimants' business, not a promotion of neutral arbitration services:
The World Intellectual Property Organization (WIPO) saw a 20% increase in the number of cybersquatting (abusive registration of trademarks as domain names) cases filed in 2005 as compared to 2004. In 2005, a total of 1,456 cybersquatting cases were filed with WIPO's Arbitration and Mediation Center. This increase represents the highest number of cybersquatting cases handled by the WIPO Center since 2001....
In the 6,349 decisions they have rendered, WIPO panels have found for the complainant in 5,327 (83.9%) cases.
Now it is not surprising that the World Intellectual Property Organization often aligns itself with intellectual property claimants against those representing the public domain, competition, or non-IP claims. It is disturbing, however, that it expresses this bias while serving as a provider of admistrative panels for the Uniform Domain Name Dispute Resolution Policy. WIPO is ICANN-accredited to provide panelists for what is supposed to be an "impartial and independent" determination of rights to a domain name.
One might already doubt the impartiality of some WIPO panelists, such as those who decided in past UDRP procedings that bodacious-tatas.com "is obviously aimed at diverting Internet users to log on to the Respondentís site in the erroneous belief that the site in question is owned by the Complainant [Tata Sons Limited]" and that vivendiuniversalsucks.com "refers to goods or services provided by the Complainant [Vivendi Universal]". Unfortunately, this release suggests that not only some panelists, but WIPO as the provider responsible for appointing panelists from its lists, has prejudged all respondents as "abusive registra[nts] of trademarks as domain names."
Small wonder, then, that in administrative proceedings where the complainant chooses the resolution forum, more than 2/3 of complainants have chosen WIPO -- a healthy business, at $500-1,250 apiece for WIPO (apart from panelist fees).